Another case of OnePlus sending personal information to a Chinese server ‘teddymobile’ occured

The emerging smartphone manufacturer OnePlus have had a been a bitter sweet moment in 2017. Not much on the sales of the devices, but concerning their software and privacy violations. The launch of the stunning flagship killers OnePlus 5T and the OnePus 5, followed a number of severe and critical accusations about customer privacy. OnePlus has been caught collecting user’s personal data such as IMEI number, telephone numbers, MAC Addresses, WiFi information, etc. without the approval of the customers. It also stored the analytics data at a server called open.oneplus.net server. Even though the data was transmitted over HTTPS, it was without user’s consent.
Read: How to disable OnePlus Analytics Tracking?
Later that year, a critical vulnerability was found which let users to get root access on OnePlus on a locked Bootloader. A backdoor exploit called EngineerMode was found installed on OnePlus stock firmware. This Engineer Mode was a backdoor to root exploit without unlocking the Bootloader. Not to forget the 911 reboot on OnePlus 5.
The end of it came when a large Credit Card breach occurred where upto 40,000 credit card data was stolen. Some users have also reported unauthorized CC purchases. This only affected users who made a purchase directly on the OnePlus site using a Credit Card in the months of November 2017 and December 2017.
Now, the OnePlus is being accused of sending personal information to a Chinese server called ‘teddymobile’. Twitter handle Elliot Alderson revealed this just a few hours ago. It states that the OnePlus clipboard is sending sensitive data including IMEI numbers, IP Addresses, Phone Numbers, to the Chinese company TeddyMobile.
According to the code @OnePlus is sending your IMEI and the phone manufacturer to a Chinese server owned by teddymobile ? pic.twitter.com/Au0u1sdpNi
— Elliot Alderson (@fs0c131y) January 25, 2018
According to the source, the OnePlus clipboard contain files like badword.txt, brackets.txt, end.txt, follow.txt, key.txt, start.txt. All these files included in the badword.zip package are some kind of Android libraries from teddymobile.
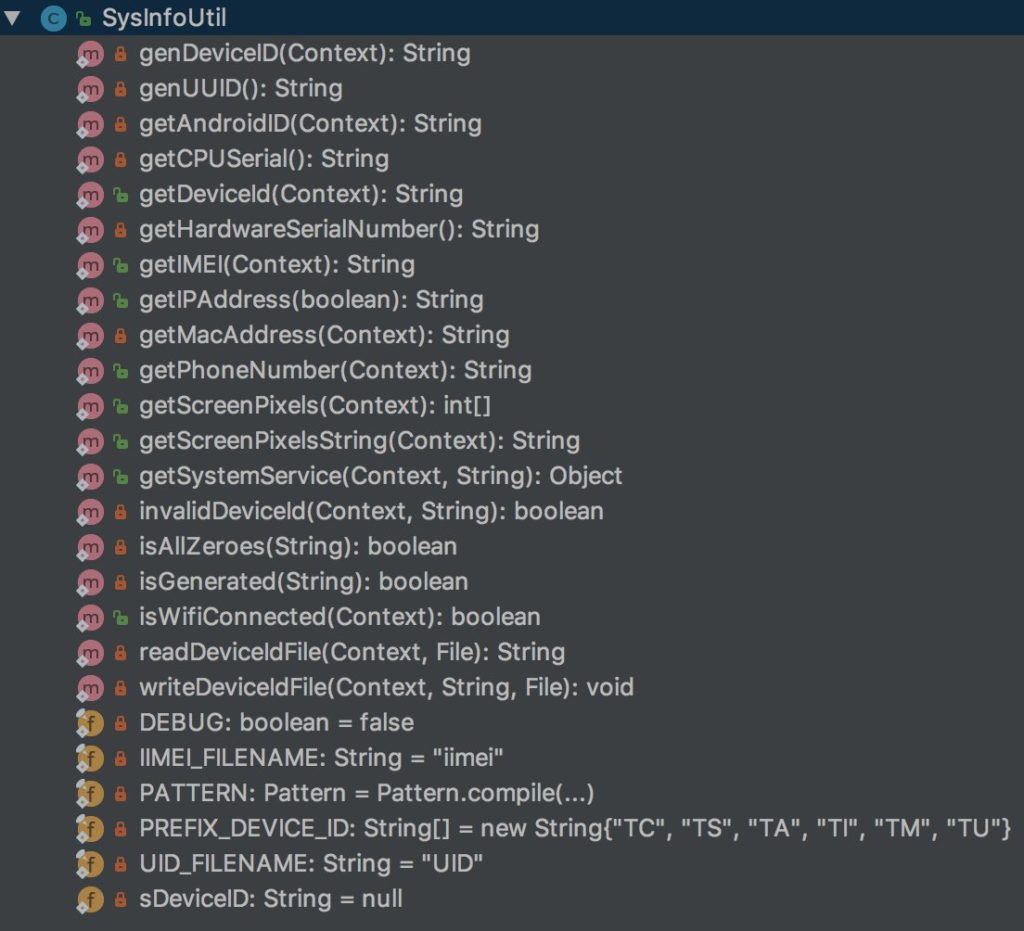
In the TeddyMobile’s package com.ted, it was found that a class called SysInfoUtil exists with the following class methods:
- getAndroidID
- getCPUSerial
- getDeviceId
- getHardwareSerialNumber
- getIMEI
- getIPAddress
- getMacAddress
- getPhoneNumber
- getScreenPixels
- more in the image
The servers are claimed to identify the data type from the clipboard app and send the personal data listed above to the TeddyMobile servers. It can also send JSON messages to their servers with a telephone and messageText fields.
Elliot asks not to copy paste any sensitive data such as Bank Account number, etc. into the clipboard until the issue is fixed. Stay tuned for more information.






